v Introduction
v Pre-Requisites
v Provisioning
of VMs
v Policy
Initiative Definition
v Remediation
v Get
List of Installed Agents
Introduction
Azure
governance has been playing vital role when we talk about Azure. Policy ensures
that resources are compliant as per the organization standard, it also
identifies non-complaint resources so that adequate action or remediation can
be applied to make resources complaint.
v Pre-Requisites
1.
To create policy initiative for Enabling monitor for Azure
VMs, you should have few VMs available or you can create using following Azure
PowerShell
2. It also enforces to have one Log analytics workspace.
v Provisioning
of VMs
To verify how Policy initiative work ,we will have two virtual machines of
type UbuntuLTS and Win2016 DataCenter
az vm create -n UbuntuVM -g cloudpiper-RG --image UbuntuLTS
--admin-username "adminuser" --admin-password
"Demouser@123" --size Standard_D2s_v3 --no-wait
az vm create -n windowsvm -g
cloudpiper-rg --image Win2016Datacenter --admin-username adminuser
--admin-password "Demouser@123" --size Standard_D2s_v3 --no-wait
Image vm-creation.jpg
Go
to Resource Group to verify does virtual machines exist there.
Create
a log analytics workspace or utilize it persists already
Policy Initiative: A Policy initiative is a
collection of policies that are oriented towards achieving a singular target.
In
this article I’ll be focusing on Enable Azure Monitor for VMs policy
initiatives which is collection of almost 10 policies are part of Azure
monitoring.
Certainly
it depends on scenarios, and on your
organizations requirement sometime its more
appropriate to use a single policy. However, if we consider future
prospects also than its will be easy to manage using Azure initiatives. Even
product group always recommends assigning initiatives, even if it contains only
one policy. Any amendments to that initiative, adding, removing or modifying
the policies, then they will be auto assigned to the right scope.
e.g. instead of managing twenty 20 diverse policies for PCI-DSS compliance, you would only be managing the initiative because all those individuals polices are being evaluated at the same time.
Practical
-> So lets jump in practical part.
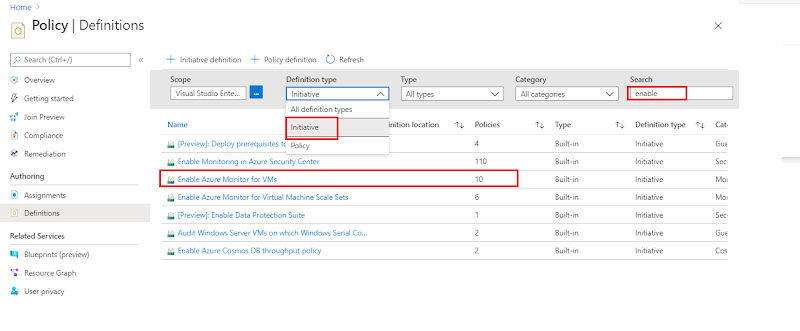
Login in https://portal.azure.com/ with your credentials and go to Policy -> Definitions as appears in following screenshot policy-definition.jpg
We
will use Enable Azure Monitor for VMs. This initiative has almost 10 policies
and is of type built-in.
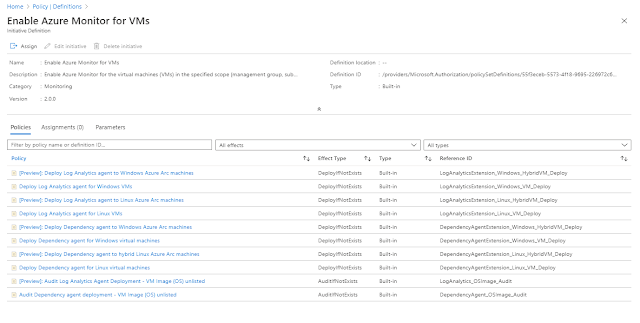
Once
you click on this initiative it opens the detailed information about all
policies exists in that. Refer an image initiative-definition.jpg
NOTE: Notice initiative definition
doesn’t have deny effect Type, though it has deployIfNotExists and
AuditIfNotExists.
Click
on assign and follow the following screen Scope.jpg
for reference fill the required details and set a scope for as per you need for instance subscription/ResourceGroup
Note:
Ensure to keep the scope of virtual machines as Subscription/cloudpiper-rg and choose the Log
Analytics workspace (Policy-initiative-law) you would have been created.
The
optional parameters are if you have your own Windows/Linux images, which could
add to the scope of this initiative.
Click
Next and Create. Refer an image create-initiative.jpg
After
successful creation it may show such message in notification
Creating
initiative assignment 'Enable Azure Monitor for VMs' in 'Visual Studio Enterprise/cloudpiper-rg' was
successful. Please note that the assignment takes around 30 minutes to take
effect.
Go to
Policy-> Assignments -> Enable Azure Monitor for VMs
Refer image Assignments.jpg
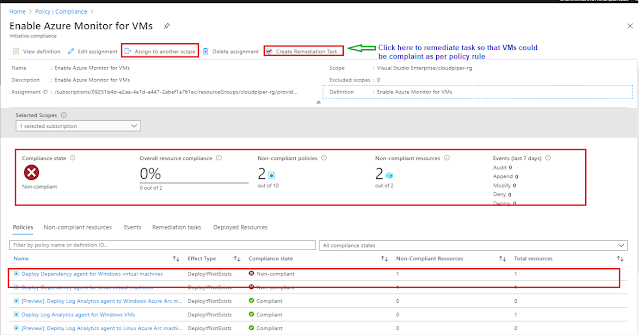
Go to
Policy-> Compliance-> Enable Azure Monitor for VMs
See the complaint state as non-complaint for 2 resources along with 2 non-complaint policies , refer an image compliance-state.jpg below for reference
Click on “Enable Azure monitor for VMs” it opens a more detailed page which contains diverse potential information along with actions which can be taken to make this complaint, like edit assignment , Assign to another scope, Create a remediation task etc. Few of them are listed
here:
v Complaint State - A newly assigned policy has ‘Not started’ state.
Refresh the view to see the latest evaluation results. If you’re seeing ‘Not
started’ for existing assignments, ensure that you have the
'Microsoft.PolicyInsights/*' RBAC permissions. If ‘Not Registered’, register
the Microsoft.PolicyInsights RP.
v Overall resource compliance - Count of compliant resource / (count of
compliant resources + non-compliant resources). To learn more, visit
https://aka.ms/policyCompliancePercentage.
v Non-complaint policies - Number of policy assignments with at least one
non-compliant resource
v Non-complaint resources- Number of unique resources that violate one or
more policy rules
Remediation
v
Click create remediation task and then click remediate. Refer an image remediation.jpg
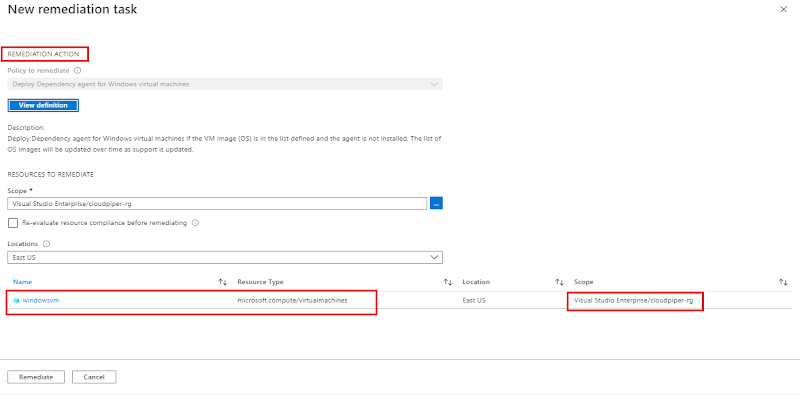 |
| Add caption |
v Once it has been succeeded, you should be able
to verify using the following command
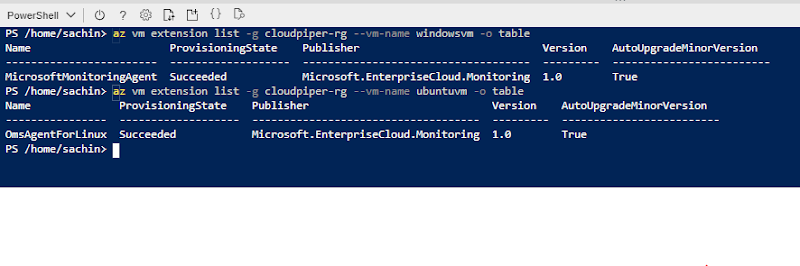
Get List of Installed Agents
az vm extension list -g
cloudpiper-rg --vm-name windowsvm -o table
az vm extension list -g
cloudpiper-rg --vm-name windowsvm -o table
az vm extension list -g
cloudpiper-rg --vm-name ubuntuvm -o table
Refer an
image Powershell.jpg
You should see the MMAExtension and DependencyAgent extensions have been installed on all VMs .
NOTE: Ensure after this lab kindly delete your resource
group as it may incur too much cost.
For more Video demonstration kindly visit my YouTube channel
*******CloudPipers******













0 comments :
Post a Comment